Standard dataset permissions
Standard datasets permissions are the same as permissions in every other section in Spider Impact. Administrators give dataset permissions to a group, and then give that group permission to view organizations. If someone is in a group that can see an organization, they can see its datasets. If someone is in a group with the “Modify Standard Permission Datasets” permission and that group can see the organization, that user will be able to modify all datasets with standard permissions in that organization.
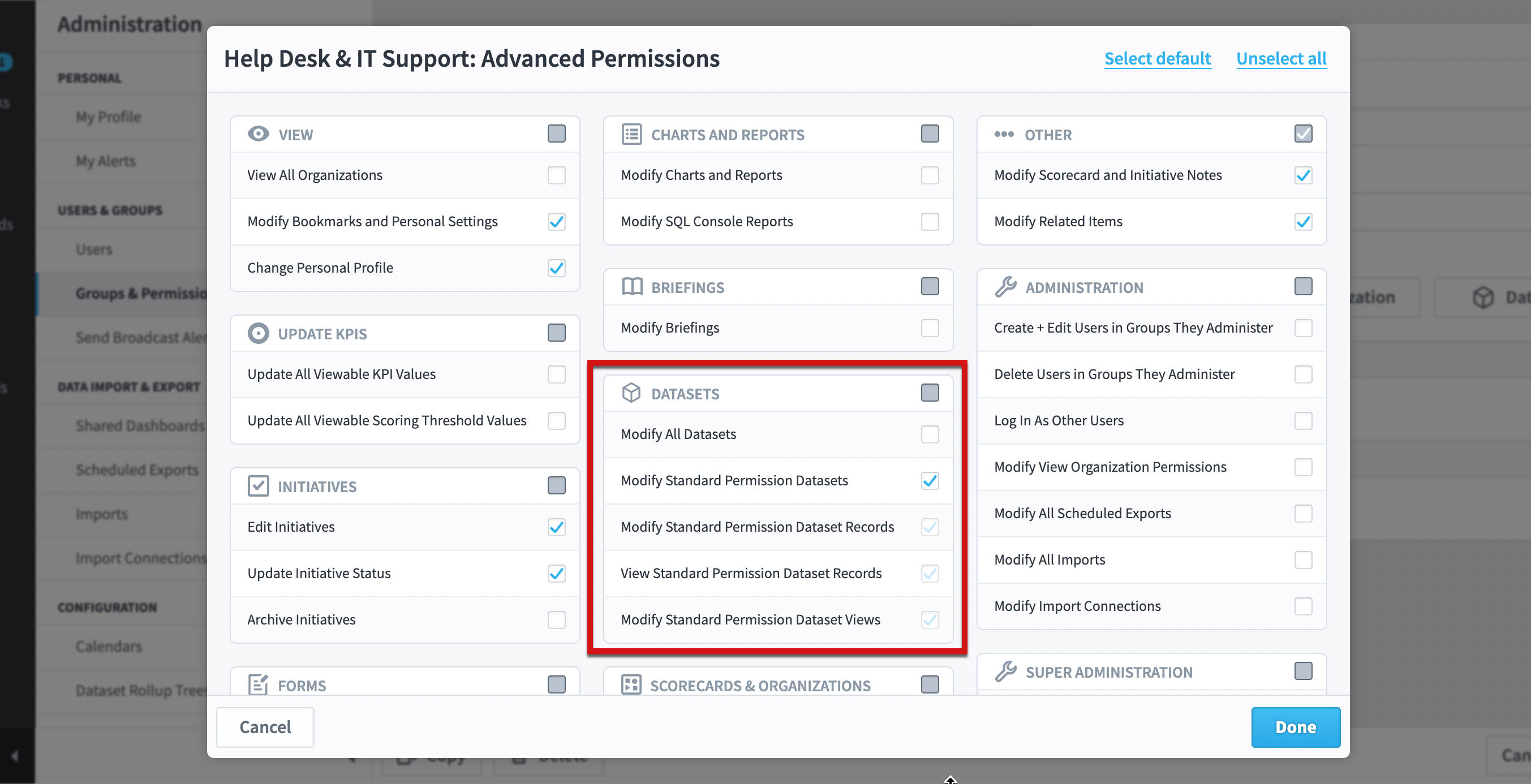
When you create a dataset, it defaults to using standard permissions. As you can see on the Datasets Edit tab, “everyone who can see this organization can see this dataset”.
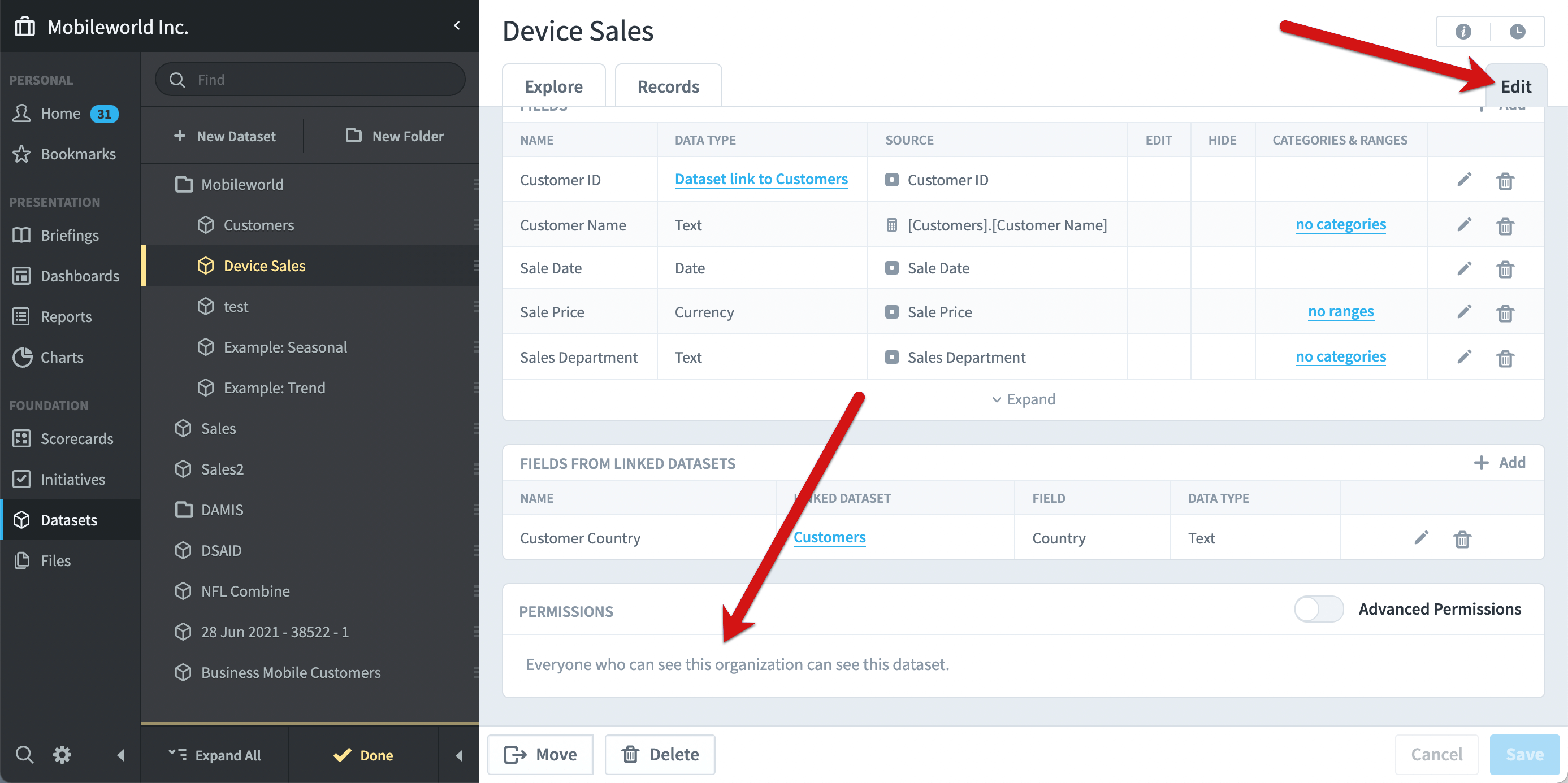
Advanced dataset permissions
There are times, however, when you don’t want people to see all of a dataset’s records. For example, you may want to allow everyone who can see the organization to only be able to see records where the “Restricted” field value is “False”. Or you may want to limit a user to only see a subset of the records based on a “Region” field.
For these datasets you can turn on Advanced permissions. When advanced permissions is on, only the users and groups who have been given explicit permission to the dataset can see it.
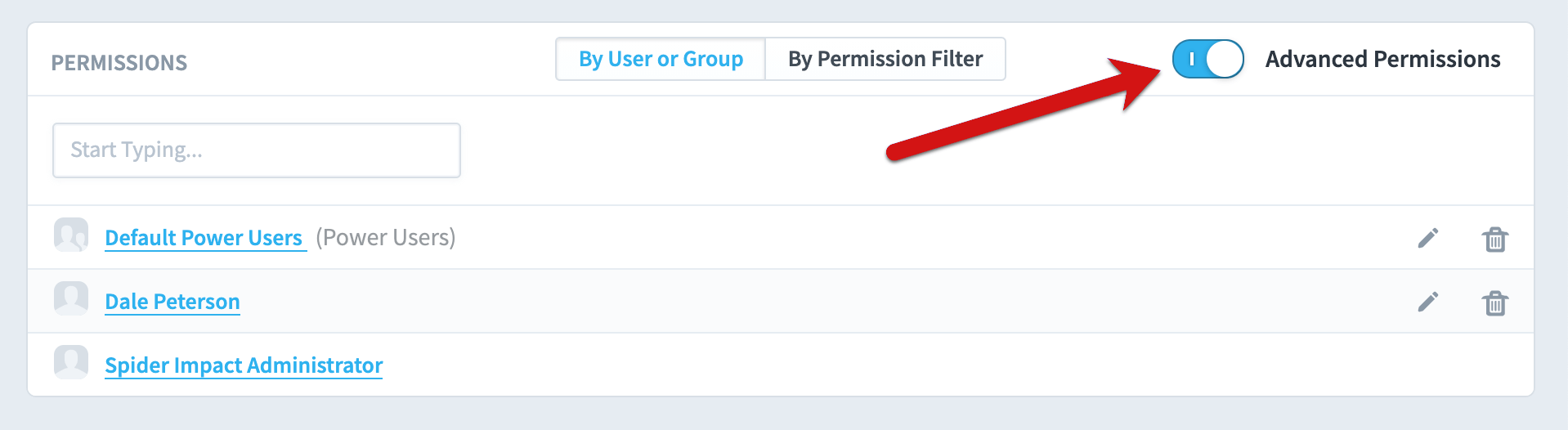
The users and groups that you add in the Permissions panel will be able to see all records by default, and they will only be able to view data. You can click on the Edit button to change this.
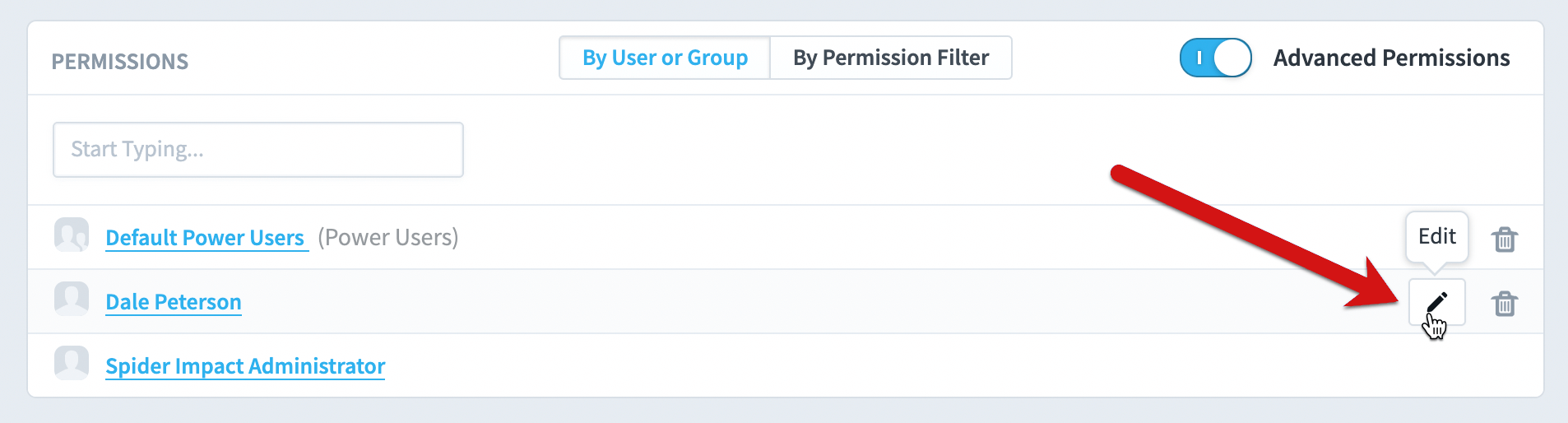
Here we can give the user any of the permissions in the purple box, and they only apply to this dataset. You can also add a permissions filter by clicking the add button in the permission filters panel.
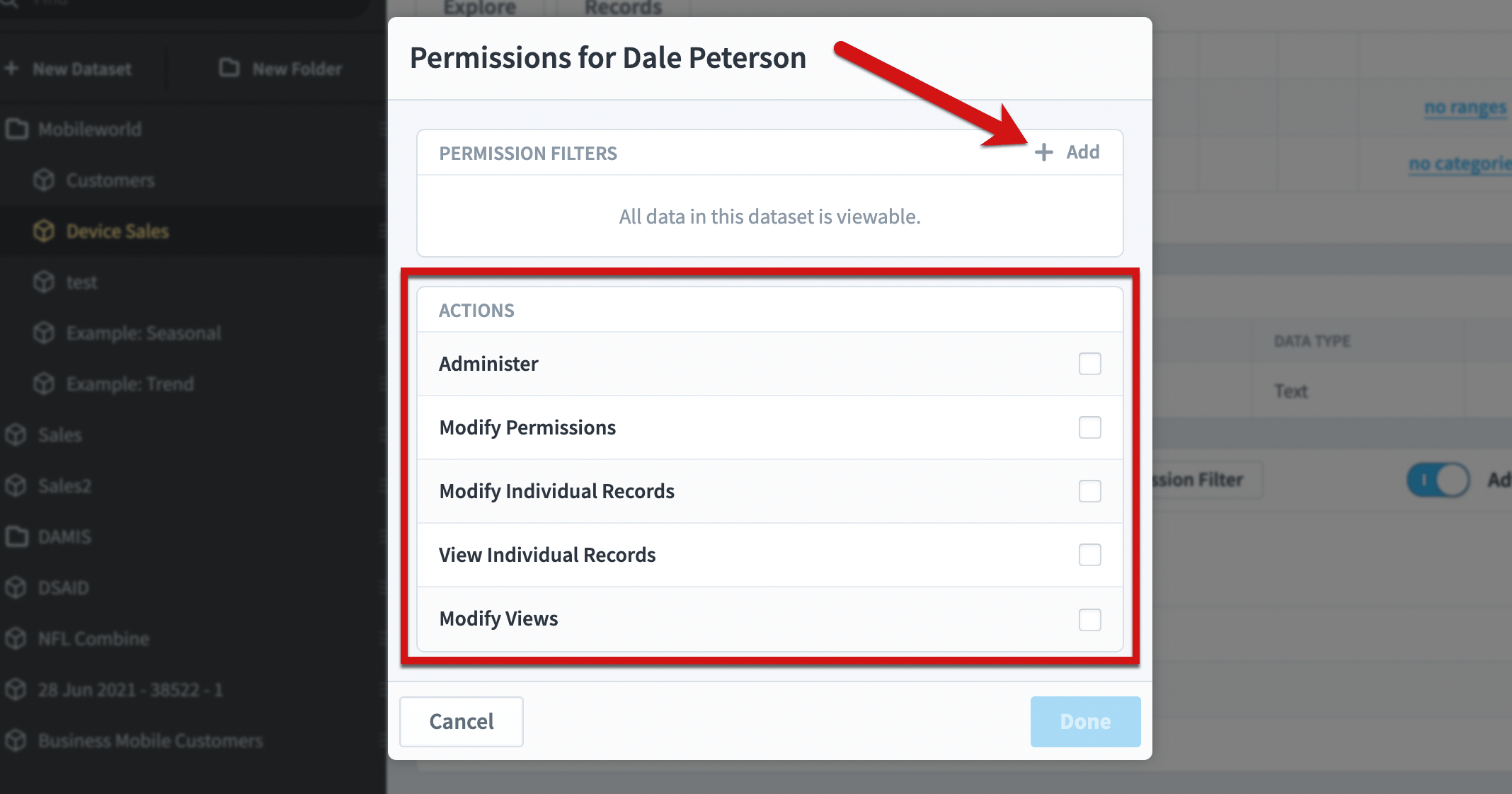
We’re going to add a filter for Sales Department = “Corporate”.
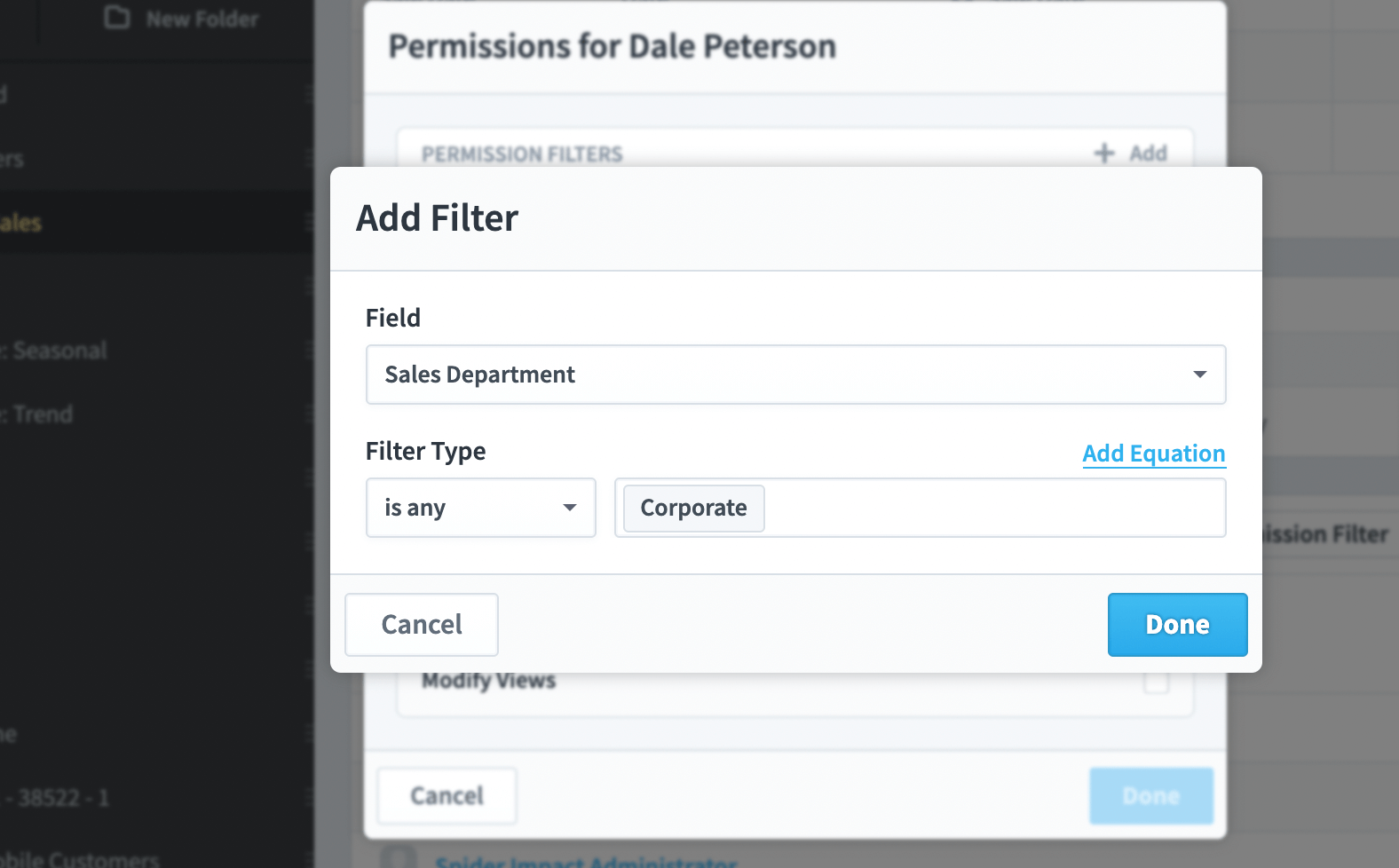
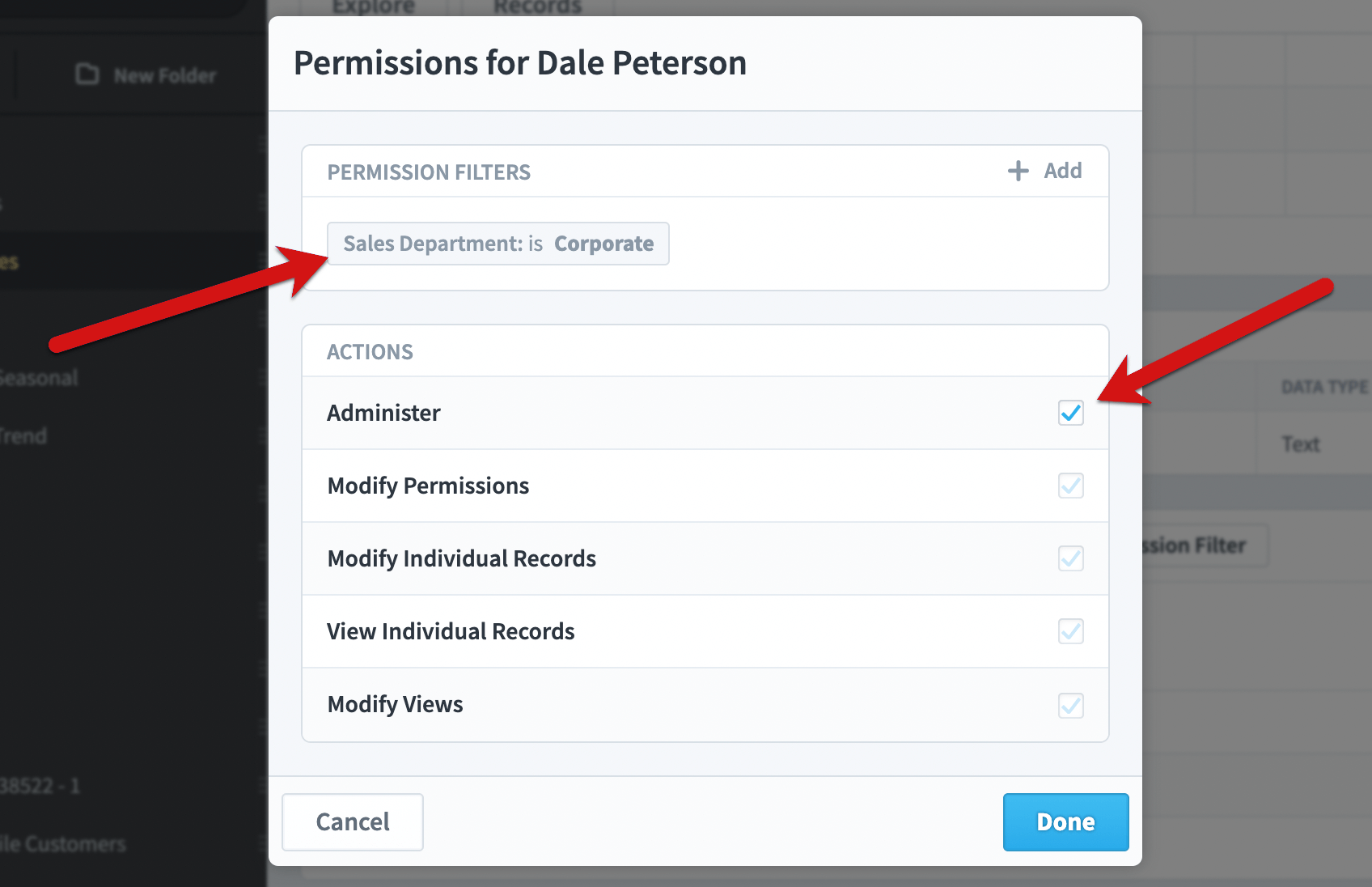
When we’re done, the dialog looks like this. Dale Peterson can administer the dataset, but he can only see records where sales department is corporate.
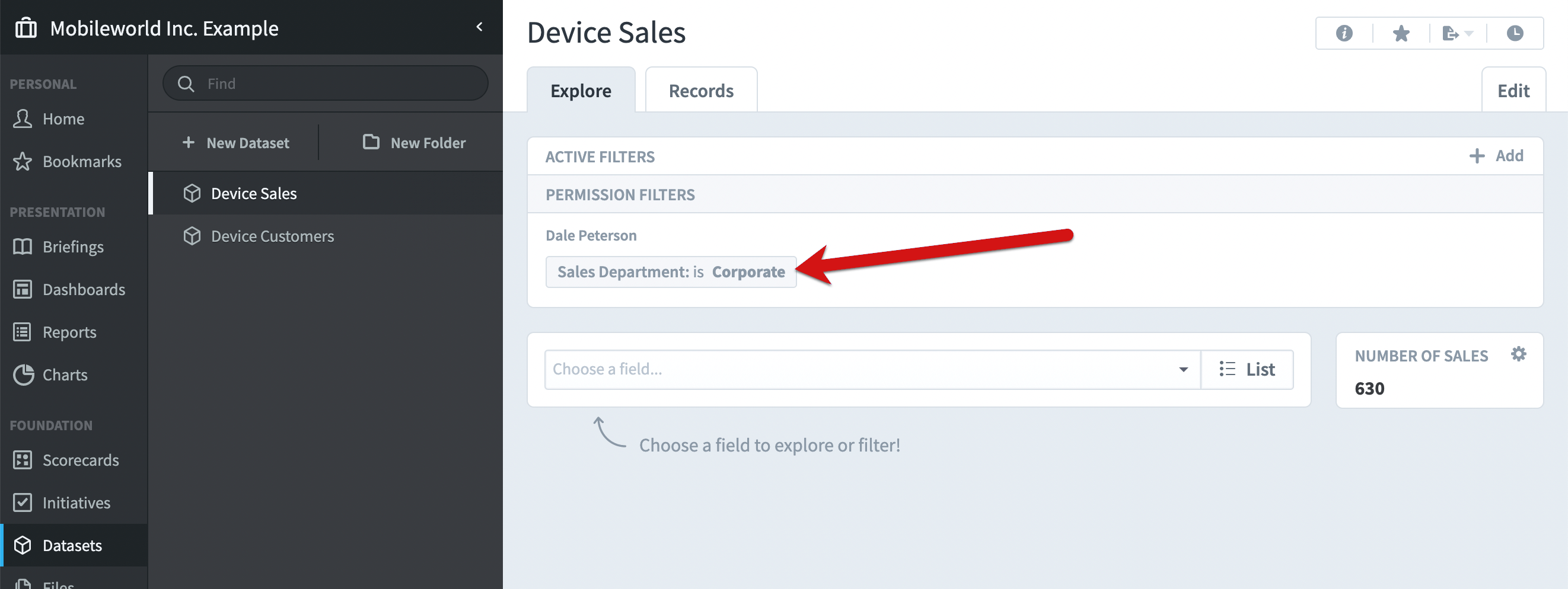
When Dale logs in, he’ll see a permission filter permanently applied to every screen that shows dataset data.
Viewing without explicit advanced permissions
There are two notable exceptions to the rule that only users and groups who are explicitly granted access can see advanced permissions datasets.
First is the “Modify All Datasets” permission. This is unchecked by default and allows members of the group to modify all datasets that the group can see, regardless of whether advanced permissions is on.
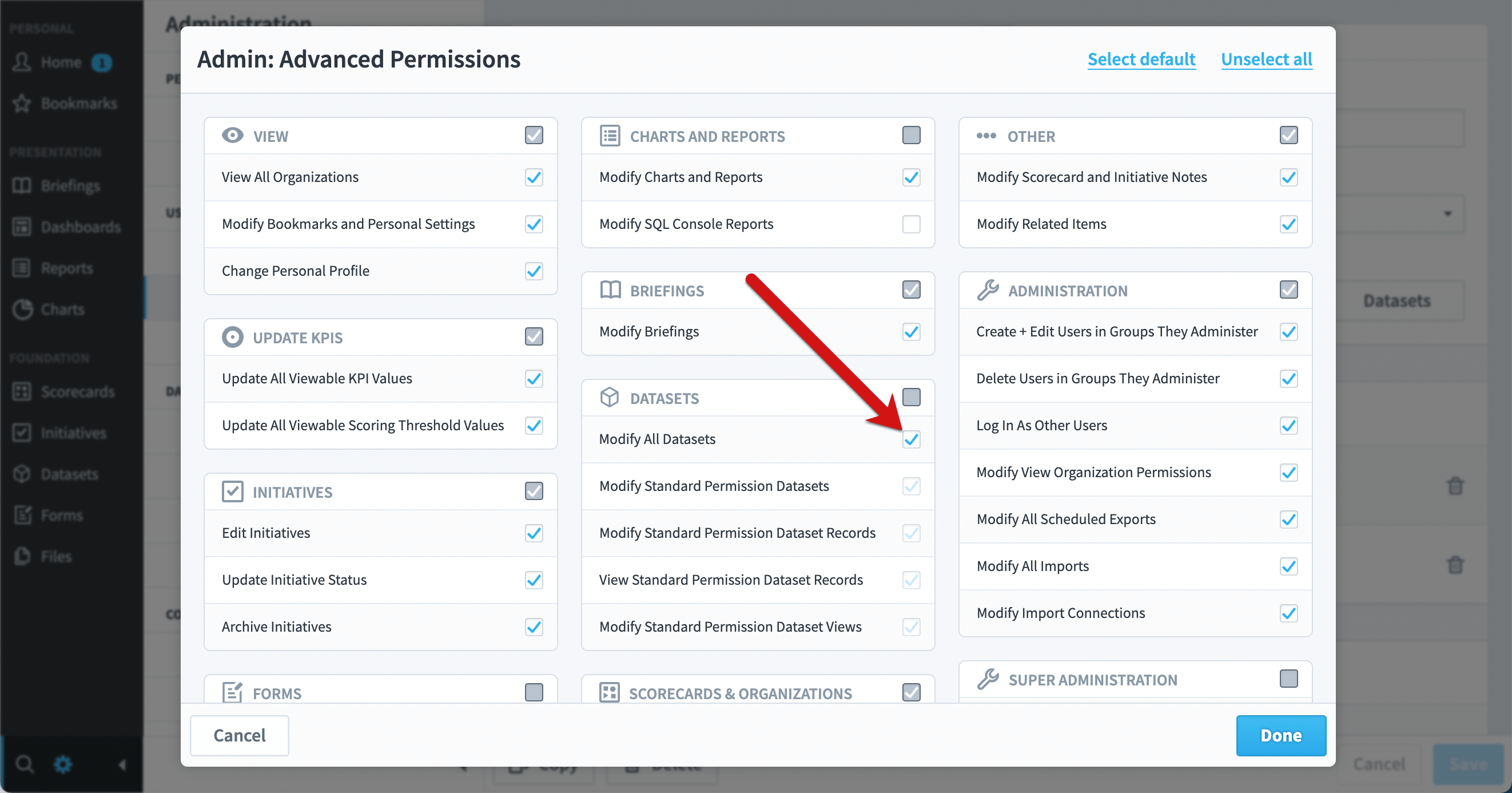
Second, you can add a user named “Everyone” when advanced permissions is on. This allows anyone who can see the dataset to view its data, and by editing the Everyone user’s permissions, you can restrict the records they can see or assign actions that every user can do.
Auditing dataset permissions
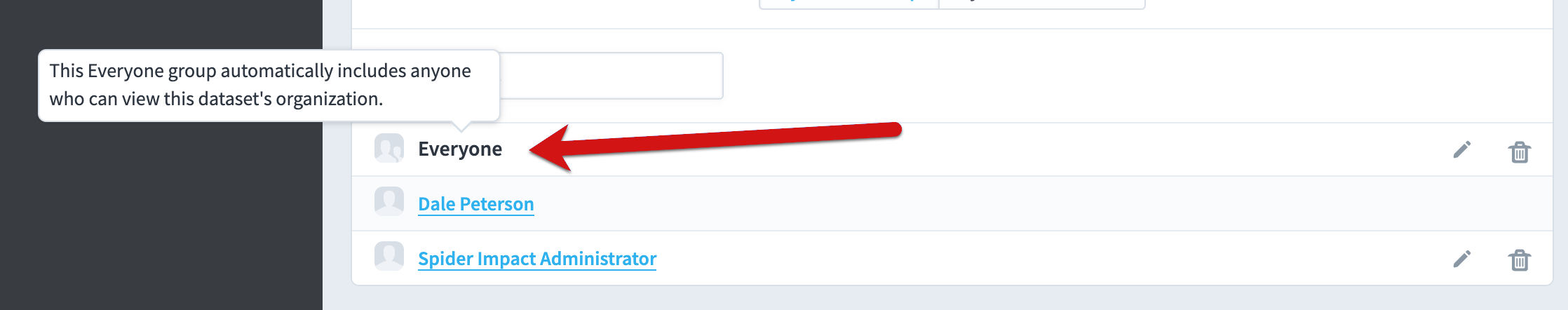
The default view for advanced permissions is “By User or Group”. This allows you to see a list of everyone who can view the dataset, and you can edit their permission by clicking on the edit button on the right.
Instead of viewing permissions “by user or group”, you can also choose to view permissions “by permission filter”. This is helpful when auditing exactly what people can see within the dataset.
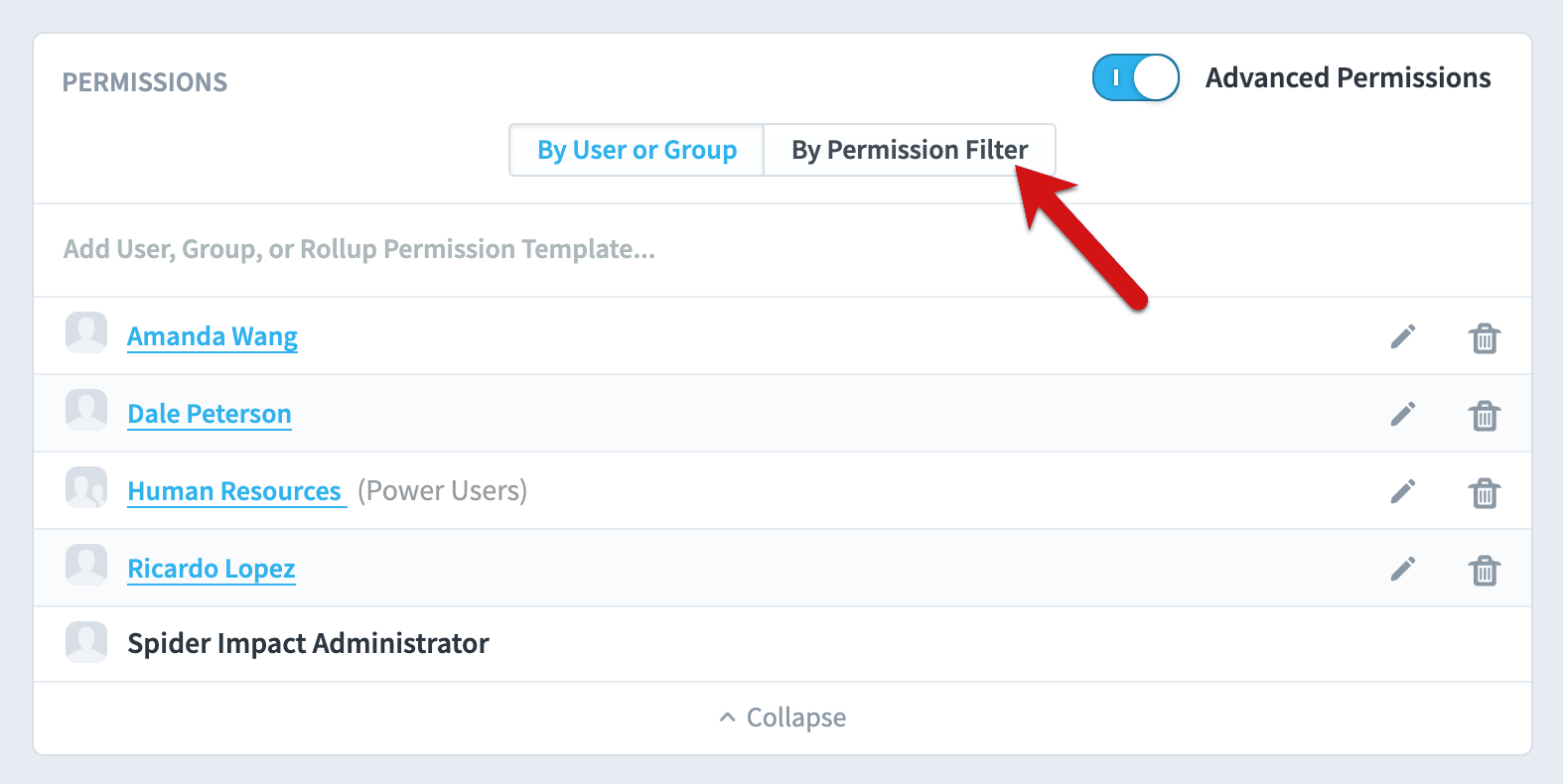
The default view is showing users and groups that have any permission filters at all. As you can see, there are two users and one group who have permission filters, which means they can’t see all of the dataset records. Just like on the “by user or group” view, you can click on the edit button on the right to see and edit their permission filters.
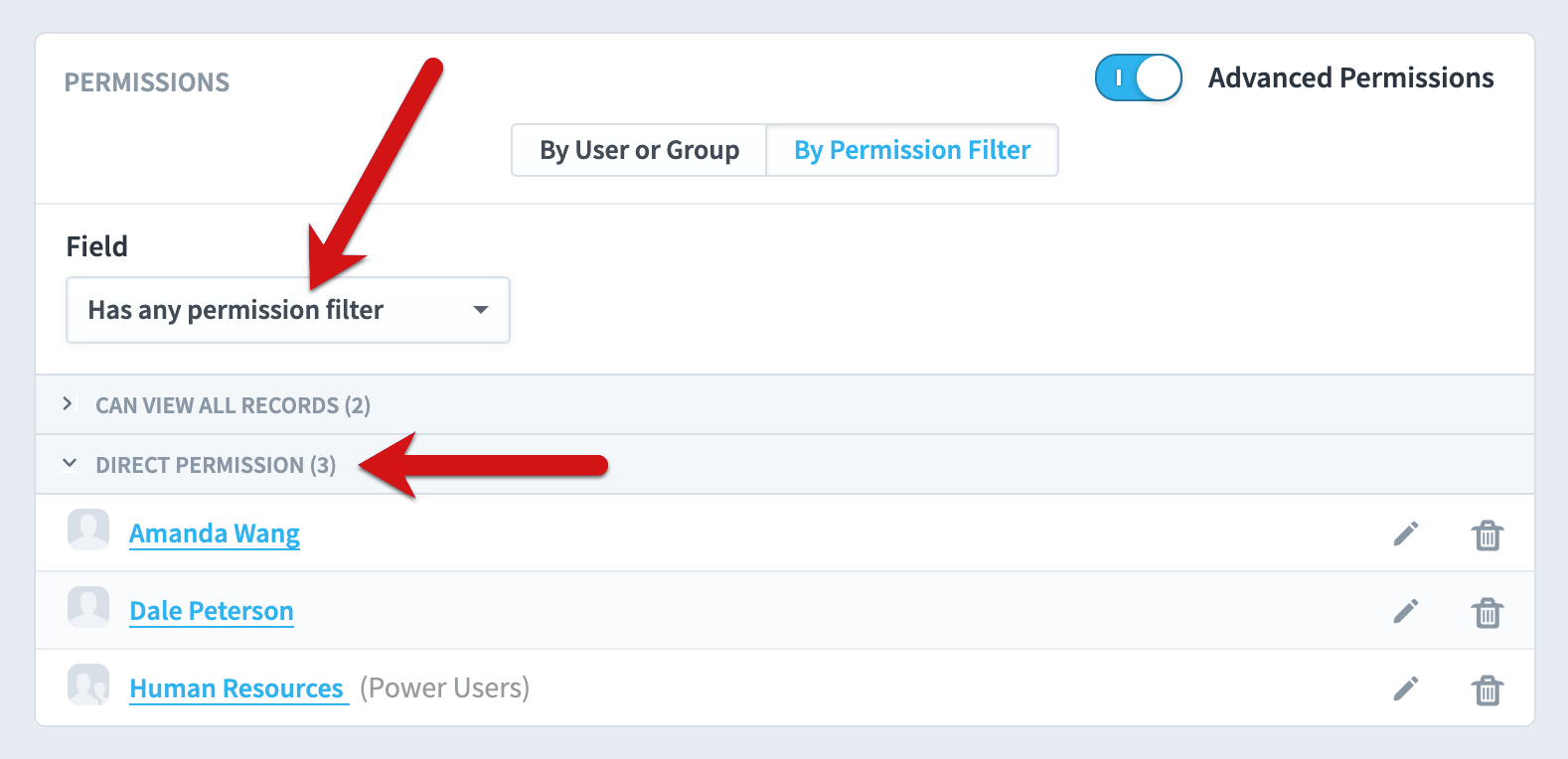
There’s also a list of users and groups who can view all records. It’s collapsed by default.
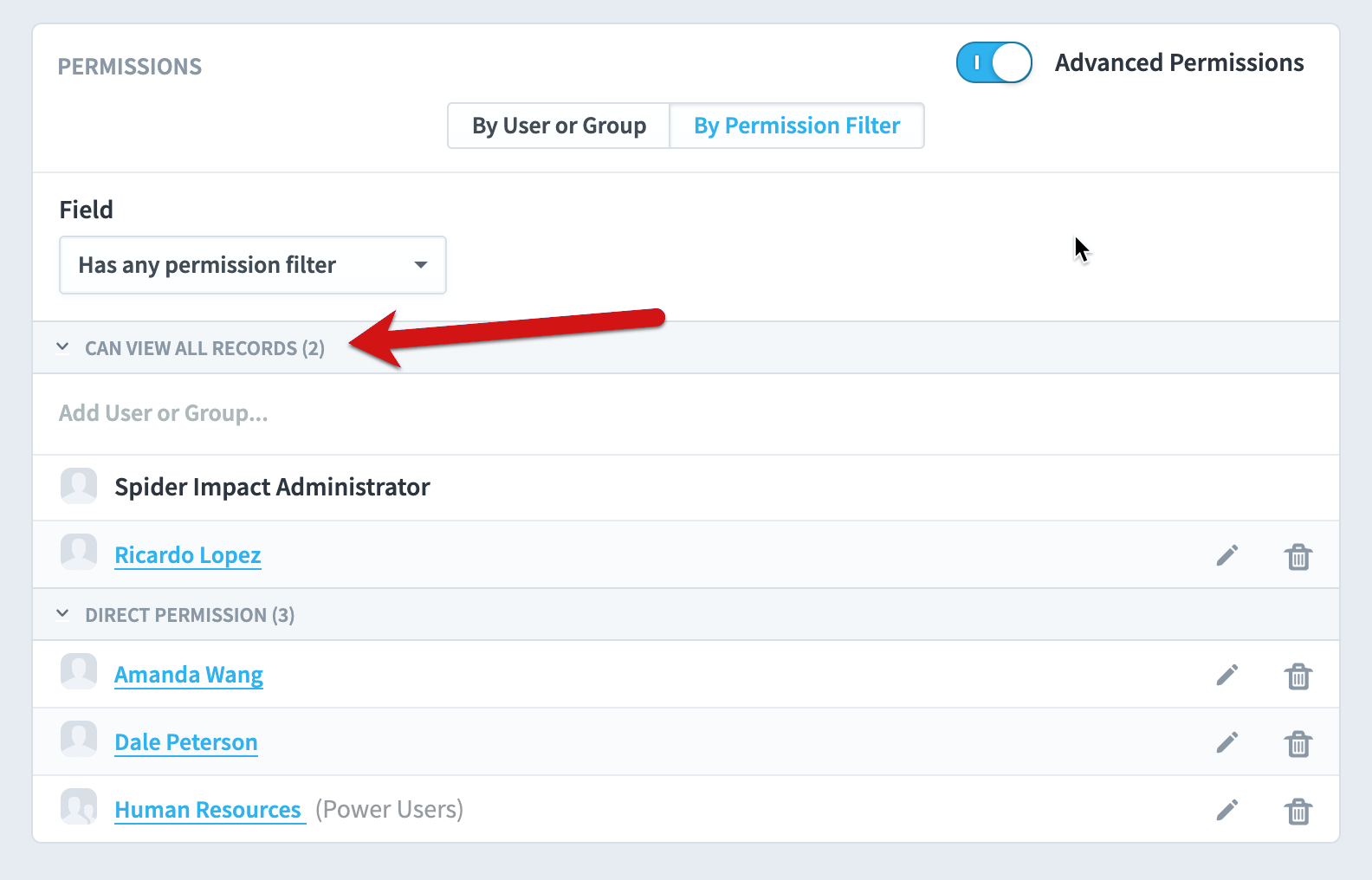
This gives us a good impression of what’s going on. There are two users or groups who can view everything, and there are three users or groups who can view only some records. We can take our permissions audit quite a bit further, though.
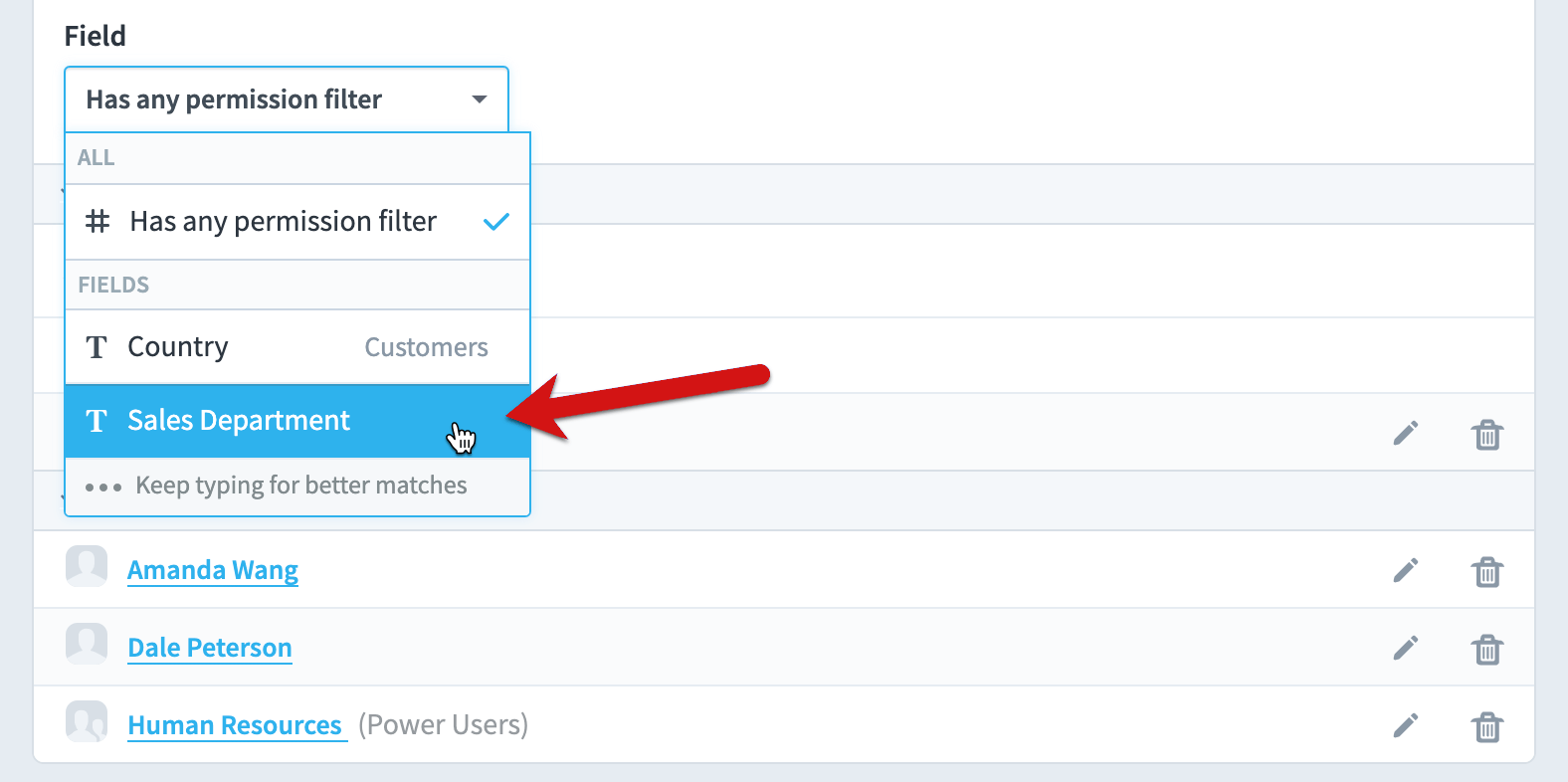
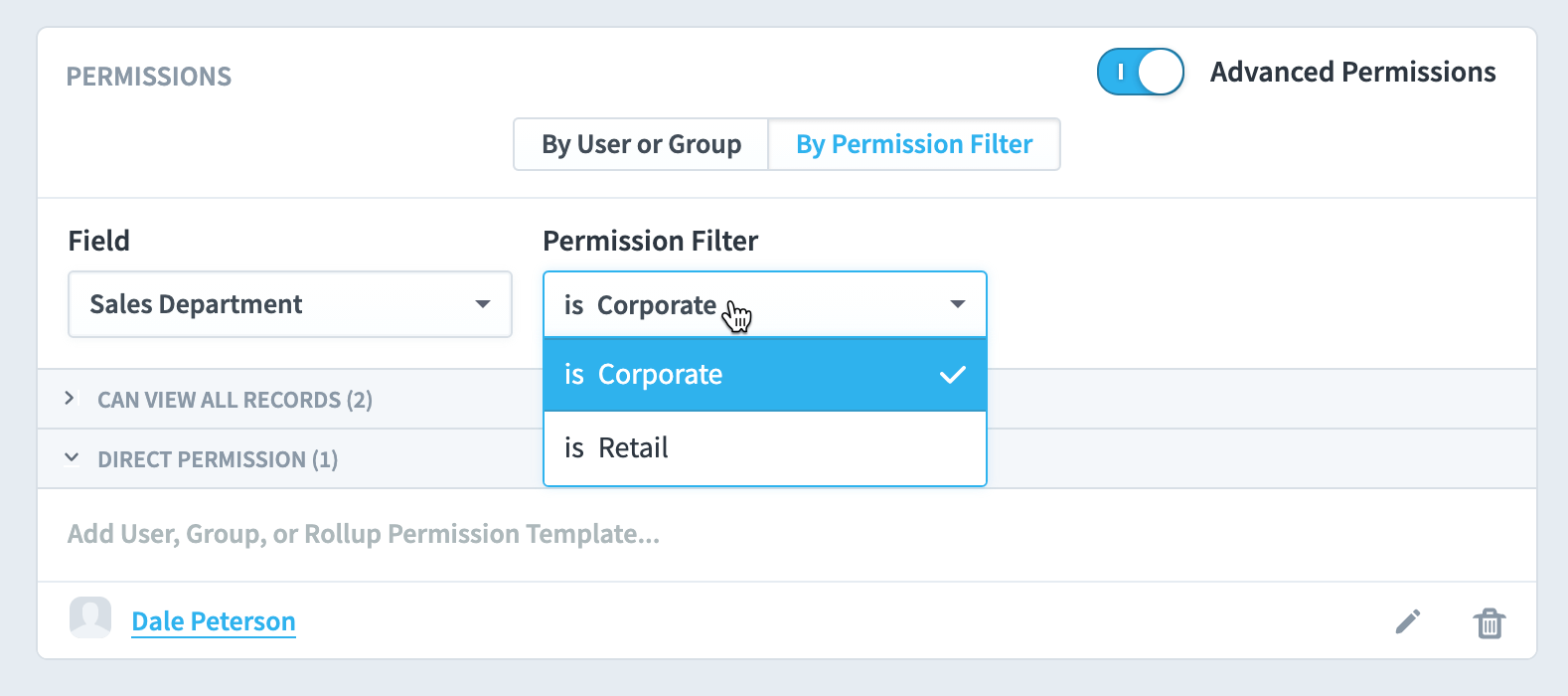
If we click the “Field” select, we can see all of the dataset’s fields that have a user or group’s permission filter applied to them. In this example, “Country” and “Sales Department” are the two fields with permission filters. We’ll choose Sales Department.
We now see that Dale Peterson has a “Sales Department is Corporate” permissions filter directly applied to him. We also see the collapsed “view all” section with the same two users who can view all records. That means there are three users in the software who can view corporate sales department records.
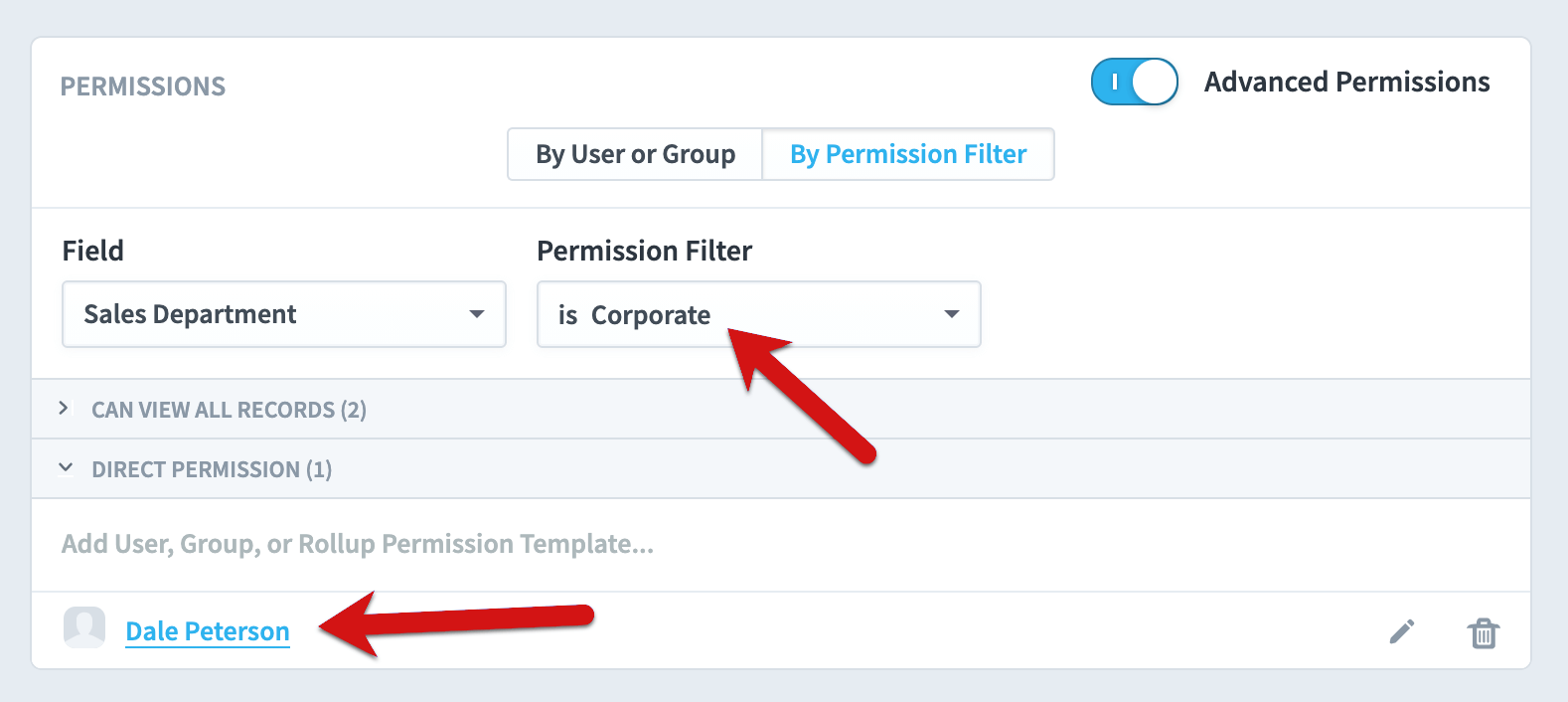
You can also quickly assign other users and groups permission to see Corporate sales records.
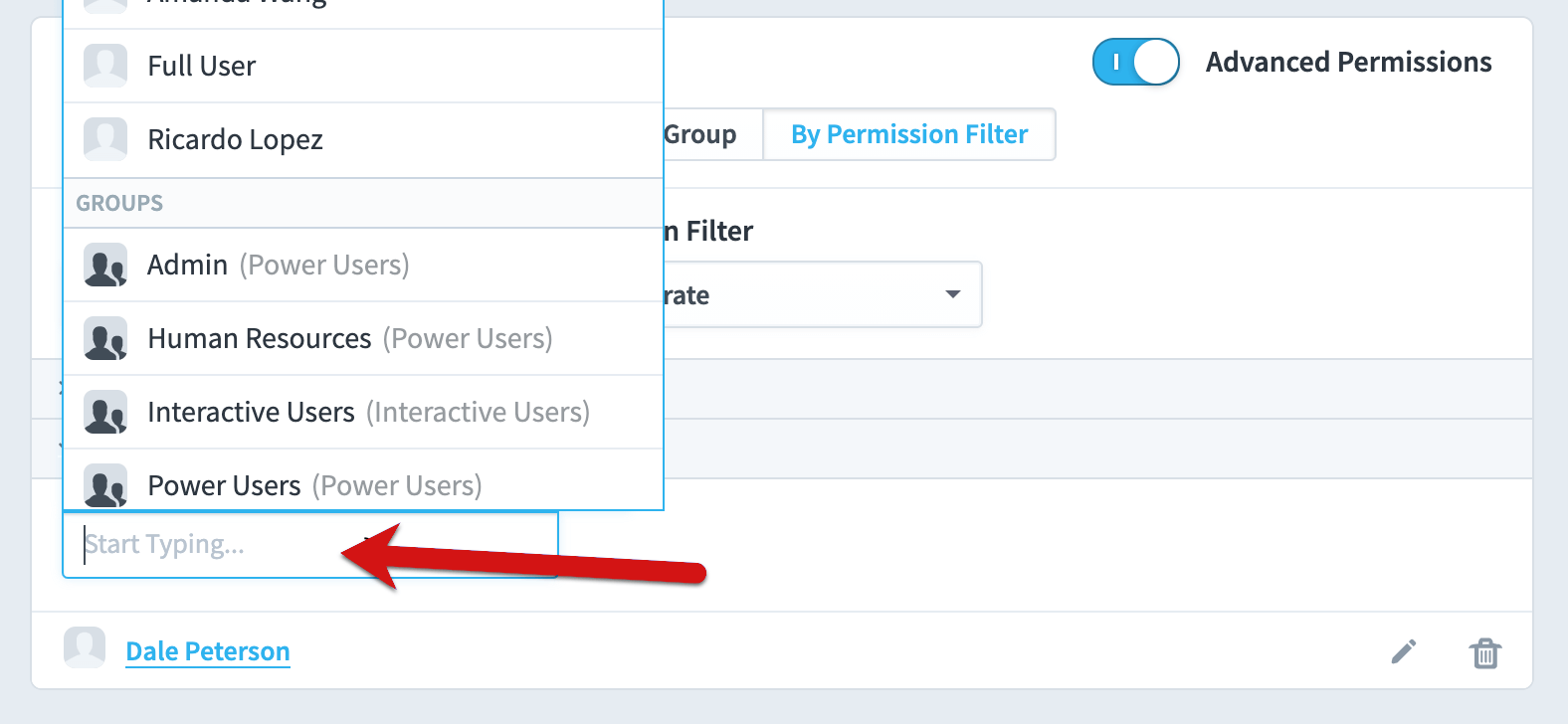
When we click the “Permission Filter” dropdown we see that users or groups also have permission filters for the sales department being retail.
By exploring your dataset permissions this way, you can quickly understand who has access to what, and you can ensure that only the correct users have access to sensitive data.
